Difference between revisions of "Discovery Job"
| Line 16: | Line 16: | ||
=== Creating a Discovery=== | === Creating a Discovery=== | ||
| − | # Navigate to '''Hornbill Administration > Home > ITOM > | + | # Navigate to '''Hornbill Administration > Home > ITOM > Job Queue''' |
# Select the '''Create New''' button | # Select the '''Create New''' button | ||
# Select '''Discover Job''' | # Select '''Discover Job''' | ||
Revision as of 08:19, 28 August 2020
| Home > ITOM > Create New Job > Discovery Job | Index |
IntroductionA Discovery is executed from a designated SIS server using Admin Credentials provided via the Hornbill KeySafe, using one of the various methods provided. Once all the devices have been discovered, dependant on configuration, a ping request will also be sent to each device. The Admin Credentials are further used for access to each devices Inventory (e.g. hardware, operating system, installed programs) using WMI via DCOM or WinRM. On successful completion, the device details will be stored within the ITOM Inventory and can be identified as managed and the Inventory viewed. |
Related Articles |
Creating a Discovery
- Navigate to Hornbill Administration > Home > ITOM > Job Queue
- Select the Create New button
- Select Discover Job
- Enter Name to identify the Job
- Select an SIS server:
- This can be a single Server or a Group
- Select the required Protocol
- Select the required Discovery Mode
- Enter the relevant Discovery Mode Settings
- Click Create button
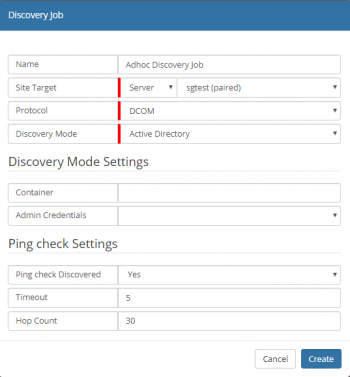
Job Properties
- Site Target [Group / Server ]
- whether the job needs to run on an SIS Group or on a single SIS/Managed CI
- Protocol
- A device is identified as discovered once it can be accessed and its inventory retrieved. This is achieved by probing its Operating System (OS) using various methods dependant on the devices Operating System. The probe will be initiated from the SIS server and does not require any software to be uploaded to the device. In order to achieve this, a protocol will be required in order for the SIS to access the device. Which protocol will depend on the OS and what is supported, in general for Windows devices WMI is used along with DCOM or WinRM, and for Linux / Unix (inc Apple Mac) Secure Shell (SSH) is used.
- Auto
- Will attempt to access the device using all of the provided protocols, in the following order; WinRM, DCOM and SSH, using the first successful one.
- WinRm
- Provides secure and firewall-friendly communications, in order to access WMI. This feature is supported on Windows 2008R2 and later and Windows 7 and later.
- DCOM
- Communication relies on Remote Procedure Calls and can be tricky to configure over firewalls. Widely supported on the Windows platform, this protocol is mainly used to access legacy devices.
- SSH
- Secure Shell is a network communication protocol that allows for remote connection between two computers to communicate and share data, commonly used but not exclusively by Linux / Unix (inc Apple Mac) devices. The protocol can be used on Windows devices, but may require additional software to be installed and configured.
- Discovery Mode
- The Discover Mode dictates the method that identifies devices on the Network. Each mode will have specific settings; these will be visible in the Discover Mode Settings section. It is only possible to have a single mode per Job, use of multiple modes will require the creation of multiple Jobs.
- Ping Check Settings
- Ping check Discovered
- [Yes / No] Check that the discovered machine is pinged - if ICMP is disabled or firewalled, then select "No"
- Timeout
- Hop Count
Job Details
Once the job has been created details will be displayed showing information relating to the job including the status of the job. Monitoring, Console and Debug Logging are provided for monitoring the progress and to aid with troubleshooting failures.
- Summary
- Shows the current status of the job and its name along with who created it and when
- Discovery Options
- Displays details of the options used by the discovery process, this will differ depending on the discovery mode that is being used
- Target Information
- Provides details of the SIS server that will facilitate the job, target machine and the security keys used
- Execution Details
- The execution details show when the job was started and completed along with any result code
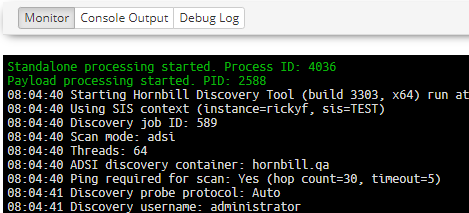
Monitor
The Monitor frame provides information relating to the execution of the job; the details shown will be dependant on the method of discovery used.
The above example shows that the discovery has started and has initiated two processes, Standalone (EspSiSExec.exe) and a Payload (ESPSisDiscovery.exe), on the SIS server.
All console output from the process is output, and confirmation of successful completion or failure will be output.
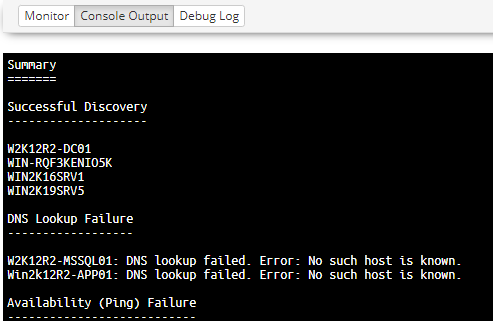
Console Output
The Console Output is accessible once the job has been completed and will contain only the output produced by the payload, including any error messages.
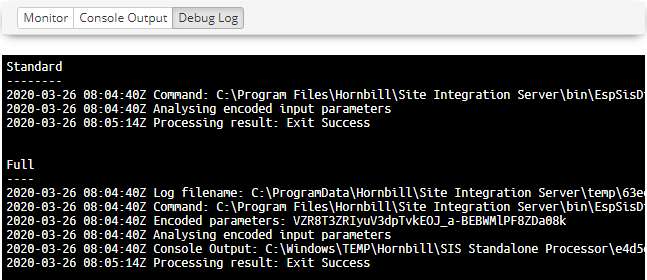
Debug Log
In cases where the Discovery may have failed or completed incorrectly, the Debug log can be used to review any errors and other technical information.
The Log provides three sections:
- Full
- Full debug log information
- Standard
- Information log entries
- Problem
- Warning and Error, entries that may identify portential problems
- The sections output will depend on the job, and thus some sections may not be available