Difference between revisions of "Template:ITOM Discovery Job Properties"
Jump to navigation
Jump to search
| Line 19: | Line 19: | ||
[[Category:ITOM]] | [[Category:ITOM]] | ||
| + | {{Template:IT Automation Job Properties}} | ||
Revision as of 06:20, 19 May 2020
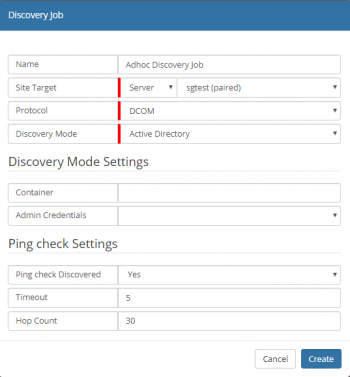
Discovery Job Properties
- Name
- Name given to identify this Discovery Job
- Site Target [Group / Server ]
- whether the job needs to run on a SIS Group or on a single SIS/Managed CI
- Protocol
- The Discovery process once a computer has been identified as a Windows device, Windows Management Instrumentation (WMI) is used to retrieve Windows Information that is used to populate the Inventory. The discovery Job will always be executed directly from the SIS server and thus needs to remotely connect with any computers that it discovers to retrieve their details. There are two methods supported, that can be utilised:
- WinRm
- Provides secure and firewall-friendly communications, in order to access WMI. This feature is supported on Windows 2008R2 and later, Windows 7 and later and later.
- DCOM
- Communication relies on Remote Procedure Calls and can be tricky to configure over firewalls.
- Discovery Mode
- The Discover Mode dictates the method that identifies devices on the Network. Each Mode will have specific settings; these will be visible in the Discover Mode Settings. It is only possible to have a single mode per Job use of multiple modes, will require the creation of multiple Jobs.
- Ping Check Settings
- Ping check Discovered
- [Yes / No] Check that the discovered machine is pinged - if ICMP is disabled or firewalled, then select "No"
- Timeout
- Hop Count
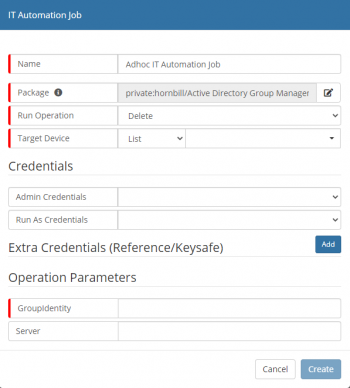
- Run Operation
- Operation to perform using the package
- Site Target
- Specify the SIS Server or Group that will facilitate the Automation Job
- Target Device
- Select the Device(s) that the Operation will target
- List
- Target Devivces are sourced from a pre-created Inventory List
- Inventory
- Select a Device from the ITOM Inventory
- Manual
- Manually entered device name, that must already exist in the ITOM Inventory and is marked as a Managed device
- Credentials
- Sourced from the KeySafe, provides the security context to be used for package deployment and execution
- Admin Credentials
- Security Context used to deploy the package onto the target device(s)
- Run As Credentials
- Security Context used to execute the package on the target device(s) (if not provided then Admin Credentials are used)
- Extra Credentials
- Optional credentials used as part of the functionality within the package
- Operation Parameters
- Once a package and a Run Operation has been selected, any related parameters will be displayed; mandatory fields are highlighted and hints may be provided in the input box.