Updating SSO SAML Metadata Configuration Action Required
We are asking all customers who have configured their SAML metadata prior to March 2021 to update their SAML configuration due to changes that have been made to Hornbill's SAML metadata and service endpoints. Basically, the redirect endpoint that your SSO service provider uses to authenticate SSO requests Hornbill users has been moved, this was a necessary change because we have changed the underlying technology stack, removing legacy PHP code and moved to a more modern front end architecture for both performance and security reasons.
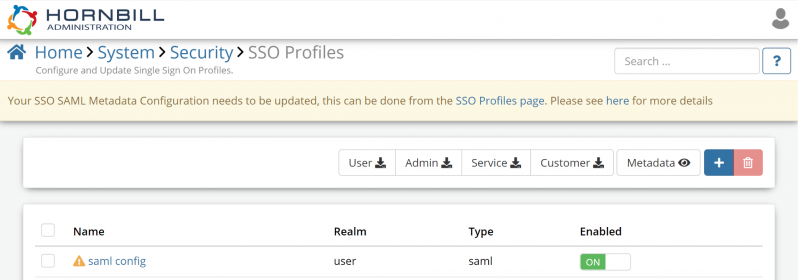
Customers who need to do this will see a banner displayed when in the Hornbill Admin tool, if you do not have this banner displayed in the admin tool no action is required.
Current customers who are using the legacy SAML metadata endpoints will still be able to login as we are currently redirecting the legacy SAML endpoint to the new endpoint. However, by updating the configuration your login will be faster, more reliable and more secure. At some point in the future the old SAML/SSO endpoint will be depreciated, we will keep an eye on the status of this over the coming weeks.
How to update the configuration
We have tried to make updating you configuration as simple as possible but it will require changes to be made on your SSO identity provider (e.g. ADFS, Azure etc). You will be required to re-import the Hornbill SAML metadata onto your identity provider. You will need to do this for each service you use SAML for in hornbill (e.g. live, admin, service, and mCatalog). This metadata can be imported alongside your current configuration on your identity provider so will not effect your users ability to login and the metadata required can be accessed by clicking the appropriate button on the SSO Profile list page in the admin tool (If your identity provider doesn't support importing metadata automatically you can view the Entity Id and Reply URL you will need by clicking on the metadata button). For more detail on how to import your Hornbill metadata to your identity provider please see the documentation here
Once you have imported the new Hornbill metadata you will be able to update your SSO profile within Hornbill, you can do this by clicking on the Update SAML Profile button against the SSO Profiles that need updating (these are marked with a Exclamation in the SSO Profile list), and clicking Yes on the Warning message, after you confirm your SAML profile will be updated and will now use the updated hornbill metadata to authenticate with your identity provider. z While you are making this change, if you have not already done so, we would also encourage you to enable the Auto Update Certificate feature, this was added to ensure that as your SSO Provider/ADFS updates its signing certificates, your Hornbill instance will automatically and securely update your SSO profiles with the new certificates which removes the need to do this manually. You can read more about how to do that here
- Note:
When using Azure as the Identity Provider, it is possible that once you have updated the configuration following the steps above, users will receive the following error when attempting to log in:
The reply URL specified in the request does not match the reply URLs configured for the application: 'https: //sso.hornbill.com/<instance_id>/live'
This happens because Azure does not properly automatically update the ACS (Assertion Consumer Service) which is the reply URL mentioned in the error message, so this needs to be actioned manually. The value for the reply URL, which needs to be manually updated on the Azure app, can be obtained by clicking the Metadata button at the top of the SSO Profiles page in Hornbill admin tool.