Updating SSO SAML Metadata Configuration
Customers who have configured their SAML metadata before March 2021 are required to update their SAML configuration due to changes made to Hornbills SAML metadata and service endpoints. This necessary change to the endpoints that your SAML Identity provider uses to authenticate SSO requests for Hornbill users is due to changes in the technology stack. These changes remove reliance on legacy PHP code, favouring a modern front end architecture providing better performance and security.
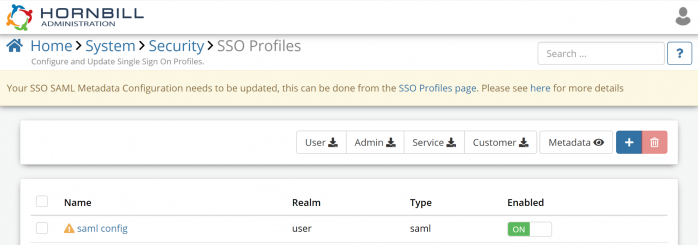
A banner will appear within the Hornbill Admin tool for all customers required to make the change; no further action is necessary for those who do not receive the banner.
An exclamation mark in a yellow triangle highlights each affected SSO configuration identified using legacy SAML metadata endpoints. Users can still log in successfully as we currently redirect the legacy endpoint to the new endpoint automatically. However, updating the configuration will speed up the user login process for end-users and provide excellent reliability and security.
Updating the Metadata Configuration
- Open the Hornbill Admin Tool
- Navigate to the following page: Home > System > Security > SSO Profiles
Accessing the Hornbill Metadata
Viewing the Metadata
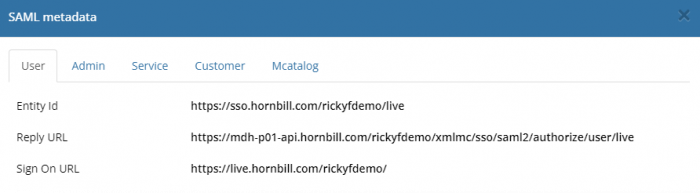
Hornbill's SAML metadata can be viewed using the following steps and the details provided used to manually update your SAML Identity Provider.
- Click on the Metadata
 Button
Button
- Select the tab for the service you are using SAML for in Hornbill
- Make a note of the Entity ID, Reply URL and Sign On URL
Downloading the Metadata
Alternatively, you can download the metadata for each service and, if supported, upload them to your SAML Identity Provider.
- When uploading the metadata to your ID Provider, a validation error asking for the Sign-on URL may appear. The URL is not required for the single sign-on configuration between the Hornbill instance and the provider and thus is not within the metadata content. To resolve the error, you will be required to enter the URL manually as detailed above.
Updating your SAML Identity Provider
To apply the metadata, you must refer to your Identity Providers documentation for the required steps. The table below contains only example data, and the following placeholders will need substituting with valid details.
- <instance> - Your Hornbill instance name
- <service> - The name of the service (live, admin, service, customer or catalogue)
- <endpoint> - API endpoint (located via the About page in the Hornbill Administraion portal)
| Entity ID | https://sso.hornbill.com/<instance>/<service> | Globally unique identifier for SAML entity. |
| Reply URL | https://<endpoint>/sso/saml2/authorize/user/<service> | The reply URL is where the application expects to receive the authentication token. This is also referred to as the “Assertion Consumer Service” (ACS) in SAML. |
| Sign-on URL | https://<service>.hornbill.com/<instance>/ | This URL contains the sign-in page for this application that will perform the service provider-initiated single sign-on. |
Updating the Hornbill SSO Profile
- Open the Hornbill Admin Tool
- Navigate to the following page: Home > System > Security > SSO Profiles
- Open the required SSO Profile
- The relevant entry will have an exclamation mark next to the entry.
- Click on the Update SAML Profile button and select Yes at the warning message
- Cick OK to confirm
Once completed, the SAML profile will be updated and use the latest Hornbill metadata to authenticate with your Identity Provider. We also encourage that the option Auto Update Certificate is enabled, which will ensure that as your Identity Provider updates its signing certificate, it will automatically and securely update on the configured Hornbill SSO Profiles. Further details can be found here