Difference between revisions of "Single Sign On Profiles"
| Line 77: | Line 77: | ||
As a general principle, we advise that the team responsible for security or administration within your company can schedule a task to renew an ADFS Server signing certificate, prior to expiry of it. We also advise that if possible, to minimise the frequency of renewing an ADFS Server signing certificate. | As a general principle, we advise that the team responsible for security or administration within your company can schedule a task to renew an ADFS Server signing certificate, prior to expiry of it. We also advise that if possible, to minimise the frequency of renewing an ADFS Server signing certificate. | ||
| + | |||
| + | Please refer to "Related Articles" in this page for information relating to SSO Profiles. | ||
Revision as of 16:41, 1 September 2017
Home > Administration > Single Sign On Profiles
IntroductionThe Single Sign On Profiles let you define integration with an identity provider such as Active Directory Federated Services (ADFS). With Single Sign On configured, authentication into Hornbill will be securely managed by your preferred authentication service. An SSO profile is created and configured in Hornbill Administration, Home > System > Security > SSO Profiles. To create and begin the configuration of a new SSO Profile, click the "+" button located at the top right of the list. |
Related Articles |
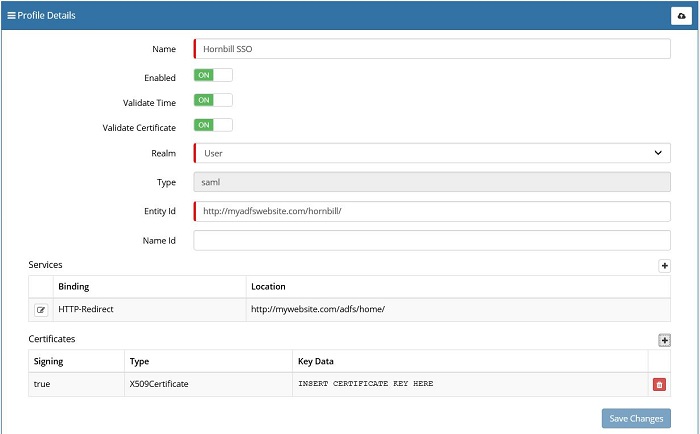
Profile Details
Populating the Profile Details and Service Bindings, aside from the Profile Name and toggle options, is completely automatic based on the Identity Provider (IdP) meta data that is generated during the configuration of your IdP. Therefore the prerequisite here is to have already performed this work within your organisations environment. An example configuration using the Microsoft ADFS 2.0 identity provider can be found here.
Processing Your IdP Meta Data
Clicking on the cloud icon on the top right of the Profile Details form will present you with a pop-up containing two fields; URL and XML. Only one of these needs to be populated.
- URL - If your IdP can present it's certificate meta data via a URL, then that URL should be pasted in the URL field, and then click "Process". Referencing the Microsoft ADFS 2.0 example, the URL that is required here is: https ://<yourserver.yourdomain.com>/Federationmetadata/2007-06/FederationMetadata.xml where "<yourserver.yourdomain.com>" is replaced by the name of your federation server.
- XML - If your IdP is not able to present it's certificate meta data via a URL, the file containing this should be opened in a text editor (e.g. Notepad ++) and copy and paste the contents into the "XML" field and then click "Process".
Upon clicking "Process", the Entity Id and Bindings will be automatically populated. All that remains is to complete the following:
Profile Details
- Name - specify a suitable name for your SSO profile
- Enabled - when you are ready to switch on SSO, toggle this to the "ON" position.
- Validate Time - toggle this to the "ON" position, this will tell Hornbill to validate that the assertion is valid at the time of issue, you should only turn this off for troubleshooting
- Validate Certificate - toggle this to the "ON" position, this will tell Hornbill to validate that the signing certificate is known and valid, you should only turn this off for troubleshooting
- Realm - for a SSO Profile facilitating single sign on for the User App, Hornbill Administration, or the Service Portal, this should be set to "User". For a SSO Profile facilitating SSO for the Customer Portal, this should be set to "Guest".
- Type - This is the secure protocol used in the SSO authentication mechanism. Only SAML 2.0 is used and supported by Hornbill.
- Name Id - If the NameID provided by the idP matches the account ID on Hornbill then this should be left blank. If however, the name ID from the idP is opaque (either static or transient) then you can use this parameter to tell Hornbill to override the NameID with a value from one of the SAML assertions attributes. This way the idP can provide a value that matches the account ID on hornbill for the user and Hornbill will use that to identify the user being authenticated
Bindings
For Web Browser Single Sign On, the bindings are used to transmit requests and responses between a service provider and an identity provider. Although these will be populated automatically based on the processing of your IdP meta data, it is possible to manually configure the following bindings:
- HTTP-Post
- HTTP-Redirect
- HTTP-Artifact
Click the "+" located towards the right of the "bindings" section. Select the type of binding and specify the location and click "OK".
Auto Provisioning
With Auto Provisioning enabled, a user account will be automatically created for the user provided they have been authenticated by the IDP.
- Name
- Template
- Enable
- Mapping
Common Issues
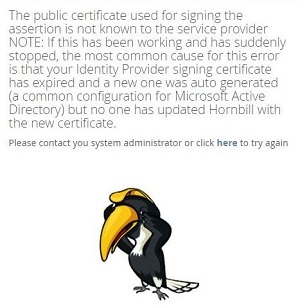
I can no longer access Hornbill
A common symptom of the error message below, is the expiry of an ADFS Server signing certificate.
This can be rectified by supplying a new certificate key for the Hornbill SSO Profile. Please contact the security or administration team within your company to request for a refreshed ADFS Server certificate key.
In the example below, clicking on + icon under Certificates section allows you to supply a new ADFS signing certificate. This can be achieved through the Admin Tool:
- Admin Tool > System > Security > SSO Profile (e.g. https://admin.hornbill.com/instance-name/security/profiles/)
As a general principle, we advise that the team responsible for security or administration within your company can schedule a task to renew an ADFS Server signing certificate, prior to expiry of it. We also advise that if possible, to minimise the frequency of renewing an ADFS Server signing certificate.
Please refer to "Related Articles" in this page for information relating to SSO Profiles.