SSO Example Config Microsoft ADFS 2.0 for User Accounts
IMPORTANT NOTICE
Information provided in this document is provided "as is" without warranty of any kind, either expressed or implied, including limitation warranties of merchantability or fitness for a particular purpose. Hornbill uses all reasonable efforts to include accurate and up-to-date information in this document; it does not, however, make any warranties or representations as to its accuracy or completeness. Hornbill will periodically add, change, improve, or update the information in this document without notice.
While we make every effort to ensure this information is both accurate and useful to you, we want to remind you that we are not experts on vendor specific iDP implementations of SAML 2.0 and are therefor not always able to provide support or troubleshooting advice with customer specific Identity Provider or Federated Directory Services implementations. We adhere strictly to the SAML 2.0:2005 standard and will talk in the language and terminology set out in that standard rather than any vendor-specific terminology which can in some cases be different and confusing if not properly understood. We expect that any troubleshooting in relation to configuring Hornbill for SSO will be carried out jointly between Hornbill and your own in-house or contracted expert that understands both SAML 2.0 and your specific federated directory services provider you have deployed within your organisation will be available. It is not practical for Hornbill's technical staff to be experts in the multitude of iDP solutions or customer-specific deployments of the same that are in use.
Hornbill Meta Data
Prior to embarking on your configuration of the necessary ADFS Relying Party Trusts as detailed below, it will be necessary to navigate to Hornbill Administration and obtain the Service Provider meta data that will be used during the configuration of your trusts. The Service Provider meta data file contains such things as the Service Provider Entity Id and Assertion Consumer Service binding that your IdP needs to communicate during the authentication process.
Log into Hornbill Administration and navigate to Home > system > Security > SSO Profiles. Located towards the top right of the list are four buttons labelled "User", "Admin", "Service", and "Customer". Clicking one of these will download the Hornbill meta data file for the associated Service URL.
You will need one or more of these files to complete the steps in the next section.
Configuring Microsoft ADFS 2.0 to work as an iDP for Hornbill User Accounts
Connect to your ADFS server and open the ADFS Management Panel
- Open AD FS 2.0 > Trusted Relationships > Relying Party Trusts
- Click Add Relying Party Trust...
- Click Start
- Click Import data about the relying party from a file' and click the browse button
- Select the remote file you downloaded from the SSO Profiles page in Hornbill Administration
- Click Next
- Enter a Display Name and click Next
- Choose Permit all users to access this relying party and click Next
- Click Close
- Open the Edit Claim rules panel (click on Edit Claim Rules...) if it doesn't open automatically
- Click Add Rule
- Select Send LDAP Attributes as Claims
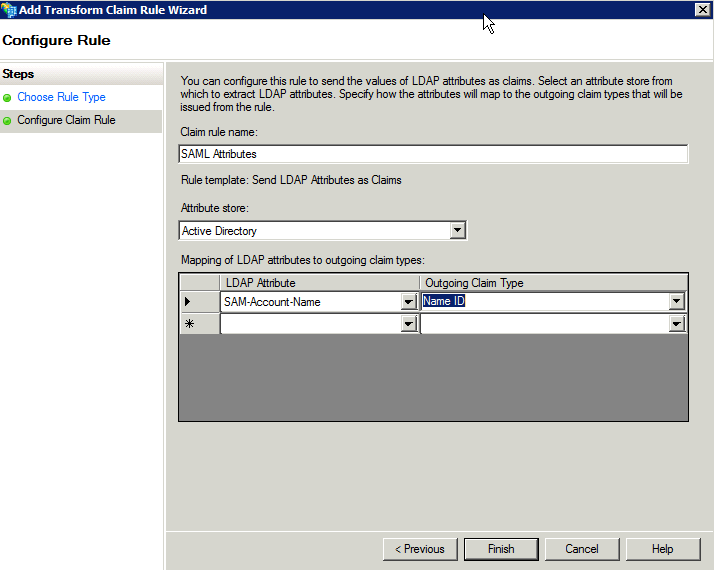
- Enter a rule name and select Active Directory as your attribute store
- You must set the name ID as this will be used by orion to identify the user
- You can add other attributes if necessary (see automatically registering with ADFS)
- Click Finish and OK to save
Auto Registration Setup
If you wish to use auto provisioning, aside from the Name ID above, you will need to specify additional claim rule mappings to send the user details from your ADFS server to Hornbill which will be used in account provisioning:
- In the ADFS Management Panel open Trust Relationships > Relying Party Trusts
- Select the Service for you User Application
- Click Edit Claim Rules..
- Click 'Edit Rule
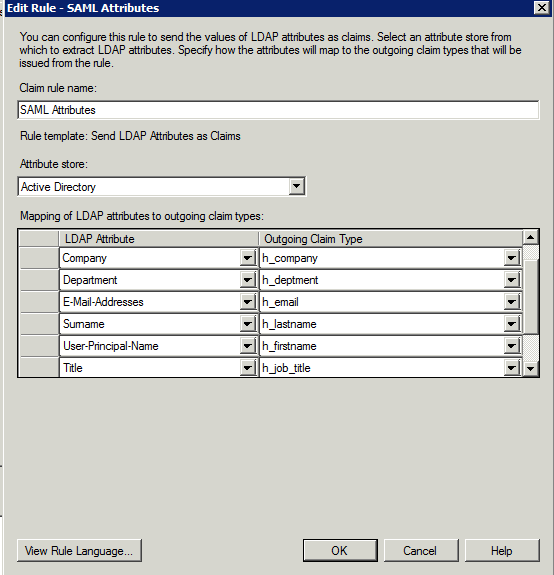
- Map your LDAP attributes to outgoing attributes (for simplicity, you should type the outgoing claim type in rather than selecting them from the drop down)
- It should look like this:
Configuring Single Sign-on in the Browser
Internet Explorer and Chrome
For the Microsoft Internet Explorer browser the following will need to be set, in order for "Authentication Pass Through" to function correctly.
- Tools > Internet Options
- Select the Security Tab
- Click on the "Local Intranet" zone icon, in order to highlight it, then use the "Sites" button.
- The default option of "Automatically detect intranet network" can be left as ticked.
- Click on the "Advanced" button.
- Use the Add button to add in the website value of: <federated services address> (for example: https://fs.hornbill.com)
NOTE: The option to "Require server verification (https:) for all sites in this zone" can remain un-ticked.
Firefox
For the Firefox browser the following will need to be set, in order for "Authentication Pass Through" to function correctly.
- Type about:config into the address bar
- Search for network.automatic-ntlm-auth.trusted-uris
- Add your federated services address, for example: 'fs.hornbill.com' to the value (if more than one value should be comma seperated)