Difference between revisions of "Azure User Import"
| Line 41: | Line 41: | ||
* https://api.github.com/repos/hornbill/goAzure2HUserImport/tags - '''Optional''' Allows access to check for the latest version of the Import Tool | * https://api.github.com/repos/hornbill/goAzure2HUserImport/tags - '''Optional''' Allows access to check for the latest version of the Import Tool | ||
<br> | <br> | ||
| − | |||
== Configuration Overview == | == Configuration Overview == | ||
Revision as of 12:23, 23 April 2019
About the Hornbill Azure User Import Utility
The utility provides a simple, safe and secure way to create user accounts on the Hornbill platform by synchronizing with accounts held in your Azure AD. The tool is designed to run behind your corporate firewall, connect to your Azure instance, query the required account information, transform and load into the Hornbill instance. The tool connects to the Hornbill and Azure instances in the cloud over HTTPS/SSL so as long as you have standard internet access then you should be able to use tool without the need to make any firewall configuration changes. The tool supports both the initial bulk import as well as incremental adds and updates. You can schedule the tool to run periodically to perform the import/update tasks as required.
The utility employs the Azure Graph API to query the contents of Azure AD. If you would like to know more about this API and it's capabilities, please refer to the relevant Microsoft documentation: Azure Graph API Information
Open Source
The Azure User Import Utility is provided open source under the Hornbill Community Licence and can be found here on GitHub
Installation Overview
Windows Installation
- Download the latest package from GitHub
- Extract zip into a folder you would like the application to run from e.g. C:\Hornbill_Import\
- Open conf.json and add in the necessary configration
- Open Command Line Prompt as Administrator
- Change Directory to the folder with goAzure2HUserImport_x86.exe C:\Hornbill_Import\
- Run the command goAzure2HUserImport_x86.exe -dryrun=true
Change "x86" to "x64" depending on your architecture
HTTP Proxies
If you use a proxy for all of your internet traffic, the HTTP_PROXY Environment variable needs to be set. The https_proxy environment variable holds the hostname or IP address of your proxy server. It is a standard environment variable and like any such variable, the specific steps you use to set it depends on your operating system.
For windows machines, it can be set from the command line using the following:
set HTTP_PROXY=HOST:PORT
Where "HOST" is the IP address or host name of your Proxy Server and "PORT" is the specific port number.
URLs to White List
Occasionally on top of setting the HTTP_PROXY variable the following URLs need to be white listed to allow access out to our network
- https://files.hornbill.com/instances/INSTANCENAME/zoneinfo - Allows access to lookup your Instance API Endpoint
- https://files.hornbill.co/instances/INSTANCENAME/zoneinfo - Backup URL for when files.hornbill.com is unavailable
- https://eurapi.hornbill.com/INSTANCENAME/xmlmc/ - This is your Instance API Endpoint, eurapi can change so you should use the endpoint defined in the previous URL
- https://api.github.com/repos/hornbill/goAzure2HUserImport/tags - Optional Allows access to check for the latest version of the Import Tool
Configuration Overview
Prior to configuring the .json file, it is advisable to read the following wiki page regarding Hornbill User Accounts as it will provide some context to the content on this page.
API Keys
There is an additional element of Hornbill configuration that we'll call upon when completing the configuration An API key needs to be created and will be used by the import utility to access your Hornbill instance.
Completing the Configuration File
A default configuration file is provided conf.json, if a configuration file is not specified as a command line argument then conf.json must exist.
{
"APIKey": "",
"InstanceId": "",
"UpdateUserType": false,
"UserRoleAction": "Create",
"AzureConf": {
"Tenant": "",
"ClientID": "",
"ClientSecret": "",
"UserFilter": "startswith(displayName,'Dave')",
"UserID": "mail",
"Debug": false,
"APIVersion":"1.6",
"Search":"groups",
"UsersByGroupID":[
{
"ObjectID":"Group Object ID",
"Name":"Group Object Name"
},
{
"ObjectID":"Second Group Object ID",
"Name":"Second Group Object Name"
}
]
},
"UserMapping":{
"userId":"{{.mail}}",
"UserType":"basic",
"Name":"{{.givenName}} {{.surname}}",
"Password":"",
"FirstName":"{{.givenName}}",
"LastName":"{{.surname}}",
"JobTitle":"",
"Site":"{{.physicalDeliverOfficeName}}",
"Phone":"{{.telephoneNumber}}",
"Email":"{{.mail}}",
"Mobile":"{{.mobile}}",
"AbsenceMessage":"",
"TimeZone":"",
"Language":"",
"DateTimeFormat":"",
"DateFormat":"",
"TimeFormat":"",
"CurrencySymbol":"",
"CountryCode":""
},
"UserAccountStatus":{
"Action":"Both",
"Enabled": false,
"Status":"active"
},
"UserProfileMapping":{
"MiddleName":"",
"JobDescription":"",
"Manager":"{{.manager}}",
"WorkPhone":"",
"Qualifications":"",
"Interests":"",
"Expertise":"",
"Gender":"",
"Dob":"",
"Nationality":"",
"Religion":"",
"HomeTelephone":"{{.telephoneNumber}}",
"SocialNetworkA":"",
"SocialNetworkB":"",
"SocialNetworkC":"",
"SocialNetworkD":"",
"SocialNetworkE":"",
"SocialNetworkF":"",
"SocialNetworkG":"",
"SocialNetworkH":"",
"PersonalInterests":"",
"homeAddress":"",
"PersonalBlog":"",
"Attrib1":"",
"Attrib2":"",
"Attrib3":"",
"Attrib4":"",
"Attrib5":"",
"Attrib6":"",
"Attrib7":"",
"Attrib8":""
}
, "UserManagerMapping":{
"Action":"Both"
, "Enabled":true
}
, "Roles":[
"Basic User Role"
]
, "SiteLookup":{
"Action":"Both"
, "Enabled": true
}
, "ImageLink":{
"Action":"Both"
, "Enabled": false
, "UploadType": "URL"
, "ImageType": "jpg"
, "URI": "http://whatever.server.com/userdb/images/{{.mail}}.jpg"
}
, "OrgLookup":{
"Action":"Both"
, "Enabled":true
, "OrgUnits":[
{
"Attribute":"{{.department}}",
"Type":2,
"Membership":"member",
"TasksView":false,
"TasksAction":false
}, {
"Attribute":"{{.companyName}}",
"Type":5,
"Membership":"member",
"TasksView":false,
"TasksAction":false
}
]
}
- An API key is set up against a user within Hornbill (accessed through: Administration > System > Organisationl Data > Users).
- There are instructions on-line on how to obtain the Secret ID
- please note that all field names are specificied as lowercase - this is to ensure smooth running for the mapped fields.
- The fields are quite self-explanatory and part of the "Details"-section (as opposed to the "About"-section [5]), most can be left as-is. The mapping is done with some templating of the format {{fieldname}}. One can be a little adventurous, for instance "{{.mgrfirstname}} - {{.mgrlastname}}" puts a space, hyphen and space between the person's manager's first and last name. One can use this to prefix or suffix the values coming from the database or indeed to set a static value (as done for example with userType and Attribute under OrgLookup for the company (Type:5)).
- The same holds here as for [4], this is regarding the "About"-section of the user's details.
- this is a non-ordered list of the organisation structure - it allows one to associate the imported user to one or more levels within the organisation. The delivered configuration file will associate each imported user with EACH of the three discernable levels (company, department and division) - depending on your requirements regarding the availability of services and such, you will likely want to manipulate this section and perhaps only leave behind the "department" level (Type: 2) with the TasksView and TasksAction set accordingly. Please note that this import only adds and not REMOVES any association.
Filtering
There are two methods of filtering users that you can configure with this tool. They are both defined in the AzureConf section of the configuration.
To import all direct User objects within one or more Azure Groups:
- AzureConf > Search : set the value of this parameter to groups
- AzureConf > UsersByGroupID : this is a JSON array of Groups to return Users from:
- ObjectID : the Object ID of the Group you want to return direct member Users from;
- Name : The Name of the Group
Using an Azure AD filter to find Users to import:
- AzureConf > Search : set the value of this parameter to users
- AzureConf > UserFilter : define an Azure filter to search for User objects. If not defined, then all User objects from your Azure AD will be returned.
Fields
These fields are those which Azure AD recognise as part of an account (eg givenName) they match LDAP variables quite nicely. However, please keep in mind that although for instance multiple email addresses can be set in Azure, only the main one in mail can be used (unless one makes amendments to the script)
Command Line Parameters
- file - Defaults to conf.json - Name of the Configuration file to load
- dryrun - Defaults to false - Set to True and the XMLMC for Create and Update users will not be called and instead the XML will be dumped to the log file, this is to aid in debugging the initial connection information.
- zone - Defaults to eur - Allows you to change the ZONE used for creating the XMLMC EndPoint URL https://{ZONE}api.hornbill.com/{INSTANCE}/
- workers - Defaults to `3` - Allows you to change the number of worker threads used to process the import, this can improve performance on slow import but using too many workers have a detriment to performance of your Hornbill instance.
Testing Overview
There is no substitute for hands-on experience when becoming familiar with the Hornbill import utilities.
The Azure User import accepts and understands a number of "Command Line Parameters" that can be used when running the utility from the command line. The most important one for testing is the -dryrun=true command. When this is specified, no information will be written to Hornbill and it allows you to confirm that the configuration is correct and that a connection to your directory server can be established. A dryrun still outputs a log file which provides you with an opportunity to review and understand any error messages that may occur.
Below are some high level steps to help you build confidence in your configuration:
- In the configuration, specify an "UserFilter" to target a single user object. (Its good practice to initially test on a single, or small set of, user objects as this allows the dryruns to complete quicker and there is less log content to sift through).
- Perform a dryrun (by executing the utility along with the -dryrun=true command line parameter).
- Review cmd output and log file for errors
- Check against "Common Error Messages" listed on the wiki and take action to rectify where necessary.
- Continue with dryrun tests until you are happy that all the errors are accounted for.
- Perform a live import with this single user object still specified i.e. set -dryrun=false
- Review user account in Hornbill and check all user properties are as expected i.e. email contains an email address etc.
- Adjust conf file user property mappings as necessary
- Loop through steps 6 - 8 as many times as is necessary until you are happy with the information being transported into the Hornbill user account properties.
- Amend the "UserFilter" and/or the scope of the "Search" variable to target the user objects required for a full import.
- Perform a dryrun
- Review cmd output and log file for errors
- Check against "Common Error Messages" listed on the wiki and take action to rectify where necessary.
- Continue with dryrun tests until you are happy that all the errors are accounted for.
Example command line:
goAzure2HUserImport.exe -dryrun=true
What Hornbill Roles are needed for the Import to Complete Successfully?
A default role is delivered with Hornbill that is designed to be used in conjunction with our range of user import utilities. The security role is called User Import and has all the necessary rights to import / update user properties.
As you may now be aware, every action within Hornbill must be performed in the context of a user account. As well as the chosen user account possessing the "user Import" role which facilitates the importing of the user accounts and updating of the user properties, this user account must posses the roles that you are associating to imported user accounts via the import utility. The above comment about roles is referring to Hornbill's security model when it comes to associating roles to user accounts, which is: Hornbill is designed to only allow the association of roles if the User who is performing the assignment of a particular role already possess the same system/application rights among the roles that they themselves possess. This security measure prevents you inflating your own rights or giving a user more rights than you have yourself.
i.e. in addition to the "User Import" role, any roles you try and assign to the user accounts being imported must be assigned to the user account logging in and running the import.
Trouble Shooting
Logging Overview
All Logging output is saved in the "log" directory which can be found in the same location as the executable. The file name contains the date and time the import was run Azure_User_Import_2015-11-06T14-26-13Z.log
Common Error Messages
Below are some common errors that you may encounter in the log file and what they mean:
- [ERROR] Error Decoding Configuration File:..... - this will be typically due to a missing quote (") or comma (,) somewhere in the configuration file. This is where an online JSON viewer/validator can come in handy rather than trawling the conf file looking for that proverbial needle in a haystack.
- [ERROR] Get https://api.github.com/repos/hornbill/goAzure2HUserImport/tags: dial tcp xx.xx.xx.xx:xxx: ........ - this most likely indicates that you have a HTTP proxy server on your network between the host running the executable and your Hornbill API endpoint. Ensure the http_proxy environment variable is set (See the section on "HTTP Proxies" for more information) and that the proxy is configured to allow this communication.
- panic: runtime error: invalid memory address or nil pointer deference [recovered]... - this error is suggesting an incorrectly specified attribute in the conf file. Where information is being obtained from a directory attribute, the attribute must be in the following format: {{.directoryAttributeName}}
- [ERROR] Unable to Create User: Invalid value for parameter '[parameter name]': The text size provided (31 characters) is greater than the maximum allowable size of 20 characters for column [column name] - the contents of your directory attribute exceed the maximum number of characters that can be placed in the Hornbill database column.
- [ERROR] Unable to Create User: The value in element <userId> did not meet the required input pattern constraints. at location '/methodCall/params/userId' - the user id contains characters that are not allowed. The User Id should be made up of alphanumeric characters. Full stops (.) and underscores (_) are also supported.
- [ERROR] Unable to Update User: Invalid value for parameter '[parameter name]': Error setting value for column '[column name]'. bad lexical cast: source type value could not be interpreted as target - this error is indicating that the contents of your directory attribute are in a format that is not compatible with the type of the Hornbill database column. For example, you will get this when trying to place text into a database field that is of type "INT" (accepts integer values only).
- [ERROR] Unable to Load LDAP Attribute: '[LDAP attribute name]' For Input Param: '[Hornbill Parameter name]' - When the import utility is unable to load a particular LDAP attribute, this means that the attribute field in your directory does not contain a value. This error will not prevent the user account being created or updated in Hornbill and can be considered more as a warning rather than an outright failure or problem.
- [ERROR] Unable to Set User Status [status name]: You have reached your user subscription limit of [xx], you will need to expand your subscription level if you wish to add more users - The utility is trying to update the user status of an existing user account from an inactive status (i.e. "archived" or "suspended") to "active" however in order for this to be successful you must have some subscriptions available.
Error Codes
- 100 - Unable to create log File
- 101 - Unable to create log folder
- 102 - Unable to Load Configuration File
Scheduling Overview
Windows
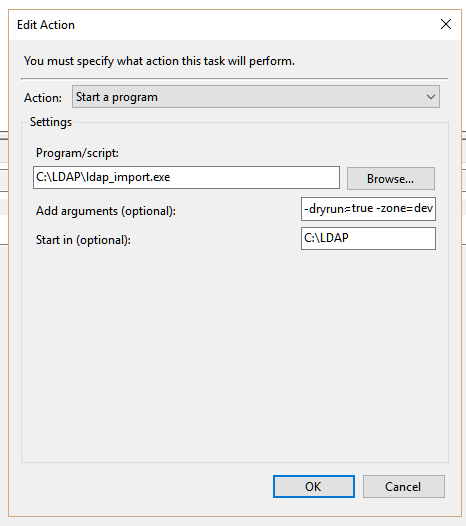
You can schedule .exe to run with any optional command line argument from Windows Task Scheduler.
- Ensure the user account running the task has rights to Azure2UserImport.exe and the containing folder.
- Make sure the Start In parameter contains the folder where the executable resides in, otherwise it will not be able to pick up the correct path. eg: